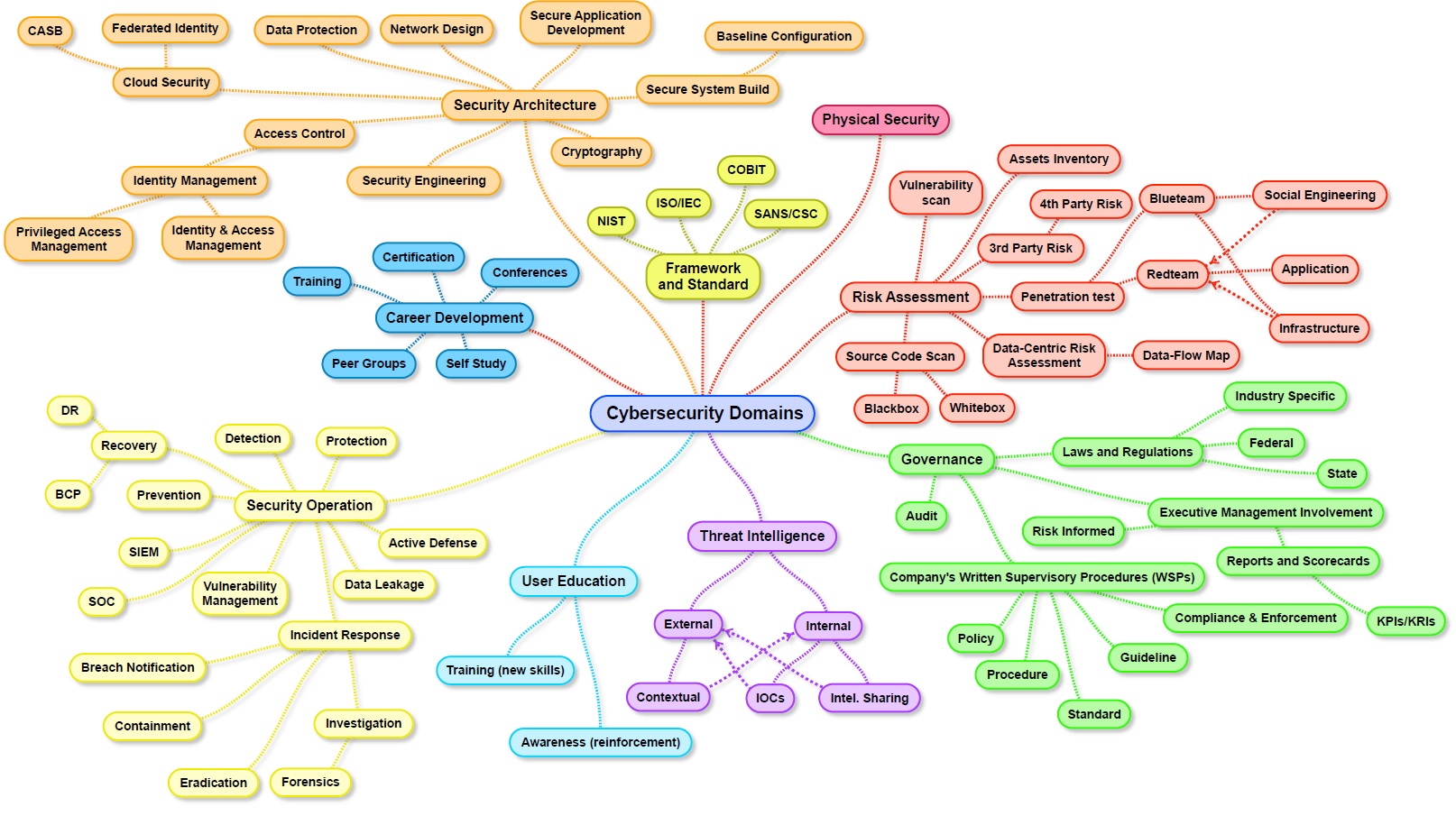
The million dollar question people always ask: how do I get a job in cyber? Unfortunately, the industry is not yet mature with established paths to entry or career growth like other professions, so your entry may still be by accident or brute force. It could also happen via a job title that does not seem security related. Let me tell you why.
I sat on a Women in Security Panel a few years ago and was surprised to discover that most of the women in the audience and on the panel fell into their roles by inadvertently or deliberately creating their own opportunities. Some of the stories included people who:
- Did work that most technical people hate: DOCUMENTATION.
- Helped their company pass an audit.
- Produced an SSL Labs report showing a failing website security grade.
- Taught themselves the new security product their company purchased.
- Were system administrators.
- Stumbled upon holes or weaknesses in their company’s systems.
- Presented research at conferences or local ISSA chapter meetings.
- Asked for cyber related project work.
- Published articles about domains of interest.
- Saved the network guy from drowning.
If you are trying to break into cyber as a graduate or transitioning from another career, your strategy should include uncovering hidden job opportunities. You may have to pivot into the field in an unconventional way.
Also consider this: depending on the company, their descriptions do not have cyber OR security in the job title because HR is often misinformed about what the role is actually about.
Some people are also under the impression that security is all about hacking. I assure you, it is not. BUT, you can hack your way into the industry.

Here are 80 back doors into cyber careers to help you expand your search:
- Miracle Worker
- IT Specialist
- IT Advisor
- Network Advisor
- Fortune Teller
- Architect
- System Administrator
- Systems Analyst
- IT Analyst
- Magician
- IT Administrator
- IT Coordinator
- IT Manager
- Systems Manager
- Spin Doctor
- Network Specialist
- Network Operator
- Network Engineer
- Network Administrator
- Fall Guy
- Professional Services Consultant
- Product Specialist
- Product Manager
- System Specialist
- Psychologist
- Administrator
- Analyst
- Sales Engineer
- Computer Operator
- Warm Body
- IT Consultant
- Consultant
- Operations Lead
- Operations Specialist
- Guinea Pig
- Operations Analyst
- Vulnerability Management
- Vulnerability Analyst
- Vulnerability Specialist
- Functional Alcoholic
- Incident Specialist
- Incident Responder
- Incident Analyst
- Systems Engineer
- Security Guy
- Malware analyst
- Reverse engineer
- Intelligence officer
- Threat analyst
- The Corner Cubicle
- Compliance analyst
- Compliance administrator
- Compliance specialist
- IT Compliance analyst
- IT Auditor
- Audit specialist
- Control specialist
- Identity and access management specialist
- Policy Analyst
- SOC analyst
- SOC engineer
- Application specialist
- Cloud specialist
- Application engineer
- Application Support
- Cloud engineer
- Cloud architect
- Server administrator
- PEN tester
- Infrastructure lead
- Infrastructure specialist
- Infrastructure engineer
- Infrastructure administrator
- Continuity Specialist
- Systems investigator
- Program Manager
- Project Manager
- Forensics analyst
- Forensics investigator
- Technical Account Manager
While some of these are obviously just for humor (although you could actually end up really playing those roles), the fact still remains that your job search may need to be expanded to include the real titles that are not comedy relief.
Depending on your interest, you could be overlooking the role you want because an HR person has it mislabeled.
Or they still use standard titles from the 1980s because that’s what they’ve always done.
You also may need to step out of your comfort zone and put yourself in positions where people want to talk to you. I’ll discuss ways to do that in a future post.
JOB ALERT!
Speaking of jobs, one of my contacts is trying to recruit a Security Engineer for a major international airline in Atlanta. Here is the job description:
Qualifications:
- 2 plus years of cyber security engineering experience preferred
- 5 plus years of IT experience preferred
- Bachelor’s Degree preferred
- ITIL preferred
- Experience with Bit9, Cylance, FireEye HX, SEP, Tripwire, BitLocker, MegaCryption, Bit9, TuFin, Tokens, and PKI Operations preferred
Responsibilities: This job requisition is for a “Domestic” position in ATL. Function as a member of the CyberThreat Unit’s (CTU) Engineering (E) function Responsible for operating EndPoint security technologies
- Shares responsibility for maintaining CTU Eng SOPs
- Accountable for managing Encryption, FIM, Firewall Rule Management, and MFA Technologies.
- Responsible for engineering and executing BitLocker, MegaCryption, Bit9, Tripwire, TuFin, Tokens, and PKI Operations
- Shares responsibility for audit support and CTU E SOPs
If interested, please send your cover letter and resume to David McCollum at dmccollum@acpros.com.
Oh and tell him where you found this role.
Have you signed up to receive blog updates?
If you found value in this post, please consider sharing!