
Part of the reason many women do not enter this field is because of the common misconception of what security professionals actually do. People watch Mr. Robot or connect with practitioners who only post about hacking, so it promotes this perception that cyber career options are off limits because that skill set is required for entry.
So, to set the record straight: I have some “hacker” qualities and tendencies, and can neither confirm nor deny that a system or few have been subject to some of said hack-foolery. YET – those abilities neither qualified me, nor prepared me to work in cyber security, and they are NOT a prerequisite in any fashion, necessarily, to understanding or working in cyber. Before I climb down off the proverbial soapbox, please let me explain.
Being a career professional in cyber security has afforded me many things – a fruitful and exciting career, the ability to function on little or no real sleep, AND a spouse. Additionally, it has afforded me the honor of mentoring from all walks of life and careers that are interested in entering the field.

I invariably always get the definitive statement “Security is so cool – I want to learn how to hack stuff…can you teach me that?”, to which I generally reply, “which do you want to do…hack or cyber security?”
After the bewilderment subsides, confusion sets in:
“I thought security and hacking were the same?”
At that point I am pulling out the holy water and rosary to commune them of their sins.
Hacking is NOT just security, and security is NOT just hacking – they are not synonymous, one in the same, of the same ilk or any other colloquialism one might use.
Worst, I often hear practitioners in the space refer to both in synonymous terms, or say something like “all you have to know how to do is code, and then you can hack and do security” …please don’t do that to us. The discipline is so much more than that.
Here’s a great illustration of what cyber entails (with more bubbles being added as teddy bears and toasters get IP addresses):
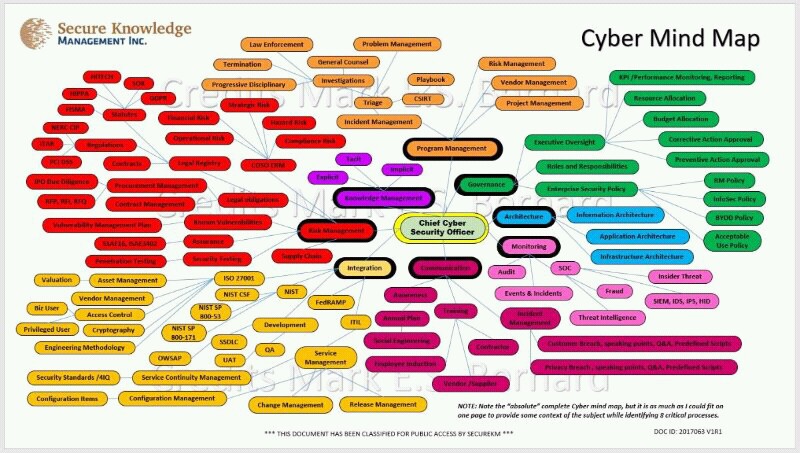
Over the course of my career, I have met many hackers (self-proclaimed and bona fide) and remain friends with many of them, and while they are extremely talented at hacking, they couldn’t secure their way out of a Starbucks with a cup of coffee.
They know very little about hardware, or systems administration, or networking or any of the other disciplines that seasoned practitioners dwell in – and many of them will admit wholeheartedly that they don’t secure stuff…they break stuff.
Very true, we as practitioners use hacking techniques to evaluate systems security and identify vulnerabilities and exploits using these techniques. This however is a VERY small part of cyber security.
If one comes into the space only wanting to hack, they will likely end up on the wrong side of the door (an iron door with bars or a slot in it), instead of the pinnacle of grace which is a cyber security career.
As practitioners, we spend much of our time trying to STOP hackers, crackers, script kiddies, etc. from impacting critical assets or defacing websites and causing reputational harm. This may be shocking to many people, but we also do a lot of reading and researching and cursing and head scratching, all to not be the next Sony or Target.

Do we need to understand how hackers operate and how they do what they do? Absolutely. Do we need to be full blown hackers to accomplish that goal? Of course not.
In fact, many of us are not at all, yet manage to be very successful in designing defensible systems and solutions able to thwart and confuse hackers. SO, scenes from Mr. Robot are not the norm…at least for most of us.
There is some whose primary job is to “hack with purpose” – we call those folks penetration or “pen” testers and they spend their days and nights looking for vulnerabilities and exploits in systems and exploiting them to the extent allowed by the engagement.
They can be identified by the dark rings surrounding their eyes and their incessant mumblings about beer and pizza. They then HOWEVER (and here is the integral part) work with the companies that they penetrated to help them fix the problems so that more nefarious hackers won’t put them in the news.
This is a call to all fellow practitioners to please, please, please – make sure those that you mentor know and understand that cyber security isn’t all sexy and stealthy and cool. It requires work and research and reading and all the things…and if you are lucky, you get to hack into some things in the process and show everyone how cool you are.

Ladies, do not let lack of hacking skills deter you from pursuing a career in the profession. This field is cross functional and has many different areas within the 8 main domains where your skill set could be useful.
Here’s a list of over 80 roles that do not contain cyber or security in the title.
You can also click Here and Here to learn about two successful women in cyber who do not spend all of their time hacking.
But before I step down off the soapbox (one foot still on the corner), let’s be clear: security is NOT just hacking!
About the Author:
On Twitter: @ProfBrager
 Paul Brager, Jr has been a contributing member of the cyber security community for over 20 years, covering the spectrum of the discipline from security architecture and defensive design to security operations and incident response. He has extensive cyber experience in oil and gas, manufacturing, chemical, and telecommunications sectors, having held various leadership, up to and including CSO of an emergency management and incident response organization. In his current capacity as a Cyber Security Architect, ICS/SCADA/EA SME for Energy and Manufacturing with a major defense firm, Mr. Brager works closely with energy, chemical and manufacturing clients to transform and mature their critical manufacturing and operating infrastructure against cyber-attack, and provide actionable and timely telemetry to assist in incident response and postmortem forensics, against some of the world’s most complex adversaries.
Paul Brager, Jr has been a contributing member of the cyber security community for over 20 years, covering the spectrum of the discipline from security architecture and defensive design to security operations and incident response. He has extensive cyber experience in oil and gas, manufacturing, chemical, and telecommunications sectors, having held various leadership, up to and including CSO of an emergency management and incident response organization. In his current capacity as a Cyber Security Architect, ICS/SCADA/EA SME for Energy and Manufacturing with a major defense firm, Mr. Brager works closely with energy, chemical and manufacturing clients to transform and mature their critical manufacturing and operating infrastructure against cyber-attack, and provide actionable and timely telemetry to assist in incident response and postmortem forensics, against some of the world’s most complex adversaries.
Paul holds a Bachelor of Science degree from Texas A&M University in Political Science, with a minor in Business, a Master’s of Science in Administration of Justice and Security (Criminal Justice/Cyber fusion) from the University of Phoenix, and is an Alpha Phi Sigma inductee since 2009. Additionally, Mr. Brager is CISSP, GICSP and CISM certified, and is currently pursuing his TOGAF and OSCP certifications, in addition to serving as an adjunct professor with the University of Phoenix, teaching cyber security courses within the IS&T program. He is currently involved as a non-voting board member of ISSA (South Houston Chapter), ISA-99 Working Committee member, ICSJWG committee member and contributor, InfraGard, OWASP, ISACA, ISC2, NSBE and various other focus groups and cyber-focused organizations, and regularly has speaking engagements with industry groups and peer collaborations. He is passionate about the security profession and looks forward to moving the needle in cyber, and helping others do the same.

